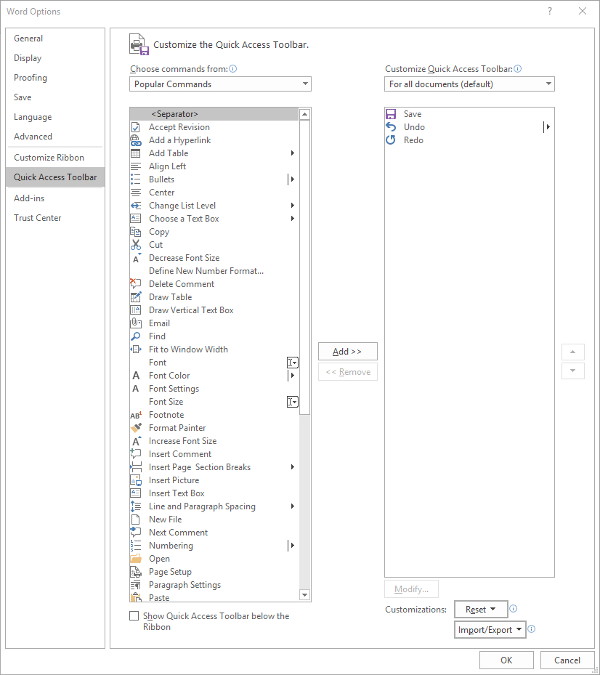
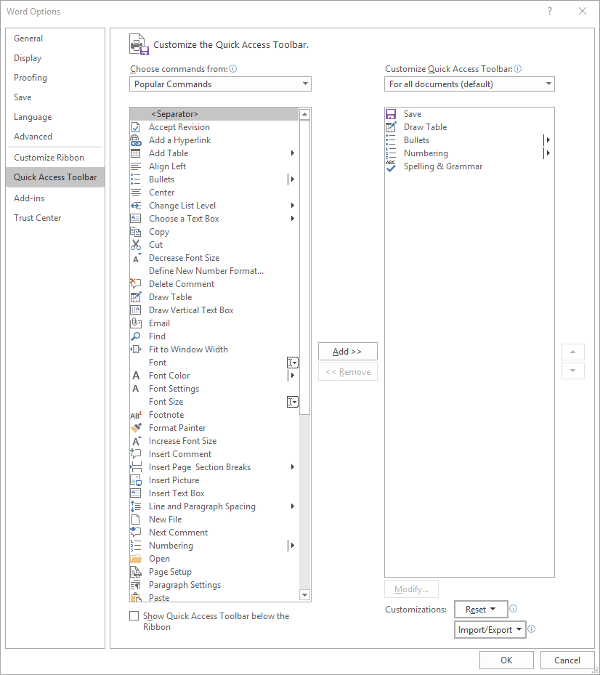
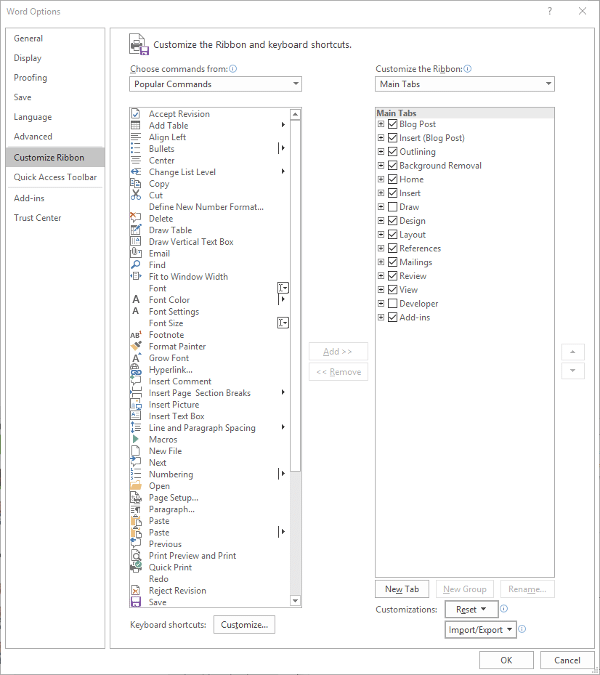
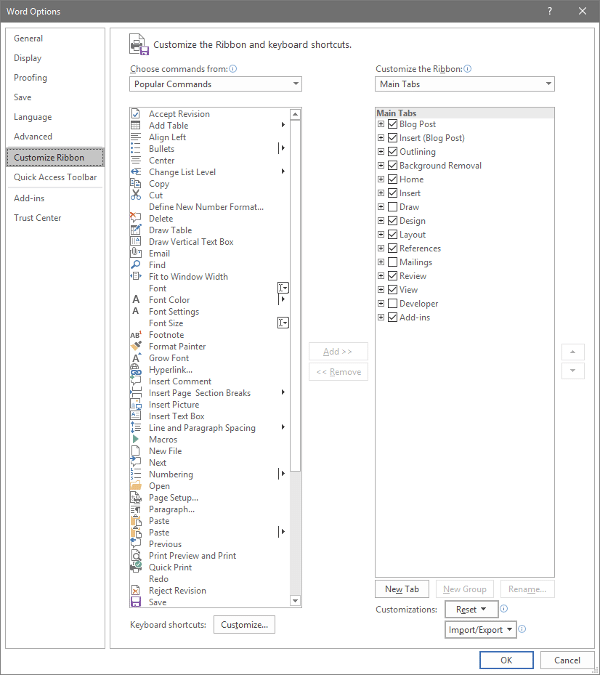
Sure - if you want to limit how you can leverage it to your business’ advantage. Here, we’ve assembled a few features that you can use to make YouTube a better resource for your business.
First Up: YouTube’s Keyboard Shortcuts
Whether you’re using YouTube as a research tool or presenting your findings in a meeting, effectively using its built-in shortcuts can make your use of the website much more productive (and, let’s face it, more impressive).
If you’re doing research, jumping back to the beginning of a video will be super handy - and is possible, by pressing the 0 (zero) key. You can also use your arrow keys to fast forward or rewind the video in five-second increments (or ten-second increments, if you hold the Ctrl key at the same time).
If you’re using YouTube as a part of a presentation, you can quickly pause and resume the video by pressing either the spacebar, or the K key. If your audience can’t quite hear what you’re presenting, you can adjust the volume using the up and down arrow keys. The M key will mute the video, and unmute it when you’re ready to hear the video again.
Starting From a Specific Point in the Video
Speaking of using YouTube as a part of your presentation, you may not always want a video to start from the very beginning. YouTube gives you a few options to do so - the easiest being grabbing the altered link to your desired time directly from YouTube.
Let’s look at this video about phishing:
https://www.youtube.com/watch?v=jfnA7UmlZkE
There’s a lot of information in this video. What if you want to focus on one specific aspect, like how phishing can be spotted? This video doesn’t dive into this aspect until just about the one-minute mark. YouTube offers a function that eliminates the need of fast-forwarding to this point. Under the Share option, the menu that appears offers a Start at option. You can select the precise time that you want your video to start. The link that appears will begin your video at the moment you have selected (unless a pesky ad gets in the way):
https://youtu.be/jfnA7UmlZkE?t=63
Search Filters to Improve Your Results
If you’re having trouble finding the right content on YouTube, there are filters that you can whittle down your results by - making it more likely that you will find more videos that fit what you are looking for. You can seek out videos that were uploaded during a specific time frame, that fall within a certain duration, and seek out specific channels, playlists, and other media types - among other filters.
YouTube can be one of the greatest resources available today... as long as you can find and share the information you need. For more ways that technology can improve your business and its processes, subscribe to our blog!